Is the brain of your cloud access control system in the right place?

Cloud-based physical access control modernizes how we manage and monitor access to our spaces. Traditional access control methods rely heavily on on-premise hardware. While no one has figured out a way to go completely hardware-free – those black reader boxes (readers) at the door are still necessary – many innovators are reducing hardware by moving components to the cloud.
We’ve identified three levels of cloud access control for you to understand as you seek solutions. As you advance through these levels, the amount of on-site hardware decreases while more of the system’s “brain” moves to the cloud. This enhances scalability, flexibility, security, and efficiency, while potentially lowering costs.
Here’s our guide to understanding how physical access control companies are increasingly shifting the “brains” of their systems to the cloud.
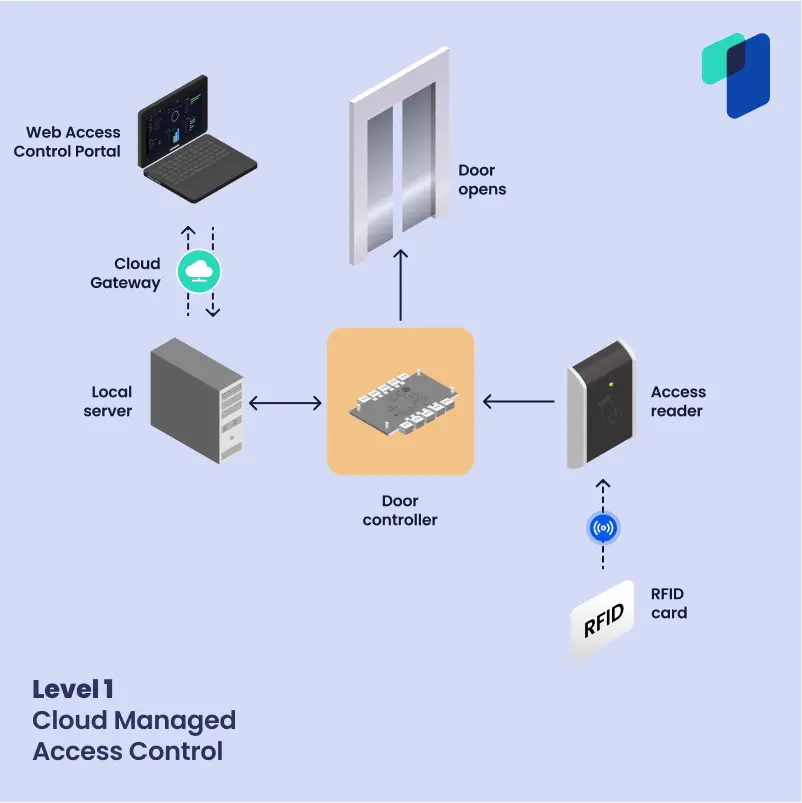
- Level 1 – Cloud-managed access control: This one feels a bit like cheating, you take your traditional on-premise access control system and slap a cloud gateway on top of it to be able to access your local servers from a web browser. Your installation still includes complex wiring, and door controllers are required to go between the door and the servers. This often stores sensitive user information and is where the “intelligence” of the system is. Requiring this ACU adds to the installation cost and complexity, as well as the scalability. It also means the system doesn’t generally have true real-time updates.
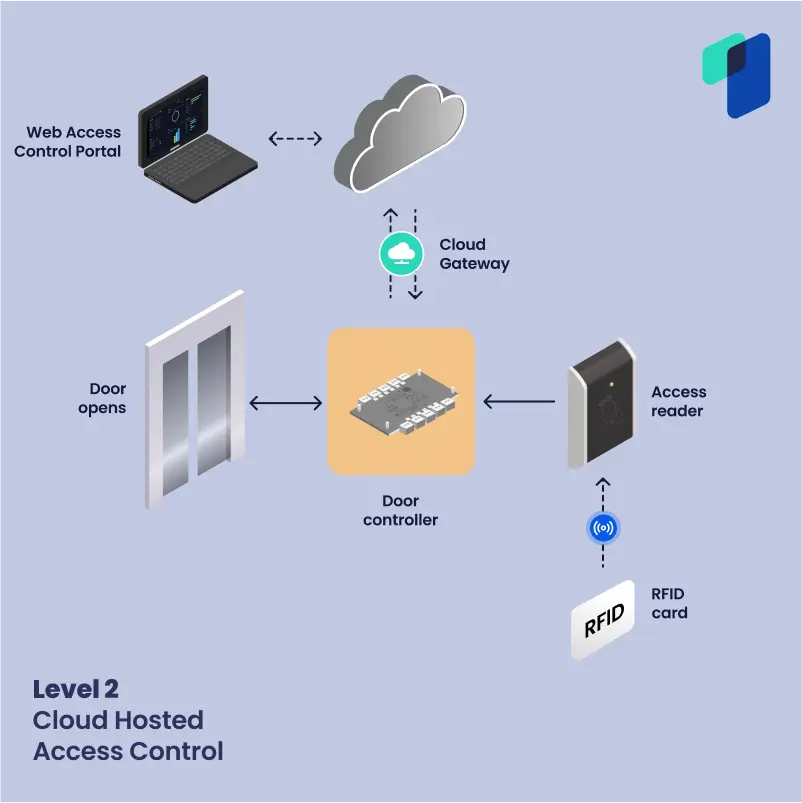
- Level 2 – Cloud-hosted Access Control aka Access Control as a Service (ACaaS): This is the most common form of modern cloud access control. The Reader communicates with a cloud hosted platform to authenticate and grant access to members. However, most of these systems still require an intermediary door controller to operate. Adding new door to your system will ultimately require adding or updating your door controllers as well, at a hefty cost.
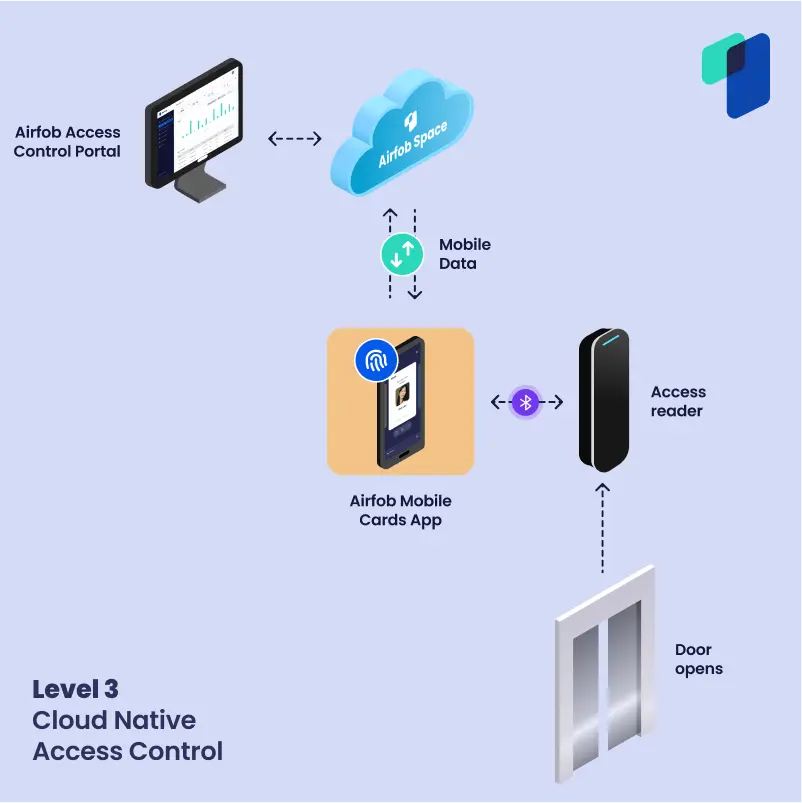
- Level 3 – Cloud-Native Access Control: This is the most advanced form of the ACaaS model that entirely bypasses your traditional door controller. When a credential is presented, the reader communicates with the cloud platform via an ethernet connection or gateway to verify the validity of the credentials. If authenticated, access is granted, and the door opens. In this case, the door controllers disappear entirely. This makes for a system that scales better: to add new doors, you simply buy a new reader. If you are using mobile credentials, you do not even need an ethernet connection between the reader and the cloud platform. When tapped on a reader, the phone communicates directly through mobile data with the cloud platform. The “intelligence” moved directly to the phone.
- Bonus Level – Biometric authentication without an expensive access terminal: Innovations in cloud access control now allow for biometric authentication using smartphones, bypassing the need for costly terminals. People can validate their mobile credentials using their phone’s built-in biometric features like face recognition or fingerprint scanning, enhancing security without specialized hardware.
- Secret Level – Bypassing readers entirely using IP cameras as relays: Many surveillance cameras that are already installed near doors already have relays built in. By connecting the camera to a cloud access control system like Airfob Space, the camera can control the door. To open the door people can use app-free, cloud-connected Link Pass credentials, or an affordable, battery-powered Airfob Tag.
FREE EBOOK
Want to learn more about access control?

Download your
free eBook!
This eBook is not only for security experts. It’s also for business owners and anyone interested in the future of access control.